Code Catastrophes: Segfault and Buffer Overflow
In the domain of programming, understanding memory-related issues is pivotal for developing robust and secure applications. Two common yet…
In the domain of programming, understanding memory-related issues is pivotal for developing robust and secure applications. Two common yet critical issues are Segmentation Fault (Segfault) and Buffer Overflow. This article explores these issues across programming languages: C, C++, elucidating with examples and analyzing the potential damage they can cause.
Segfault:
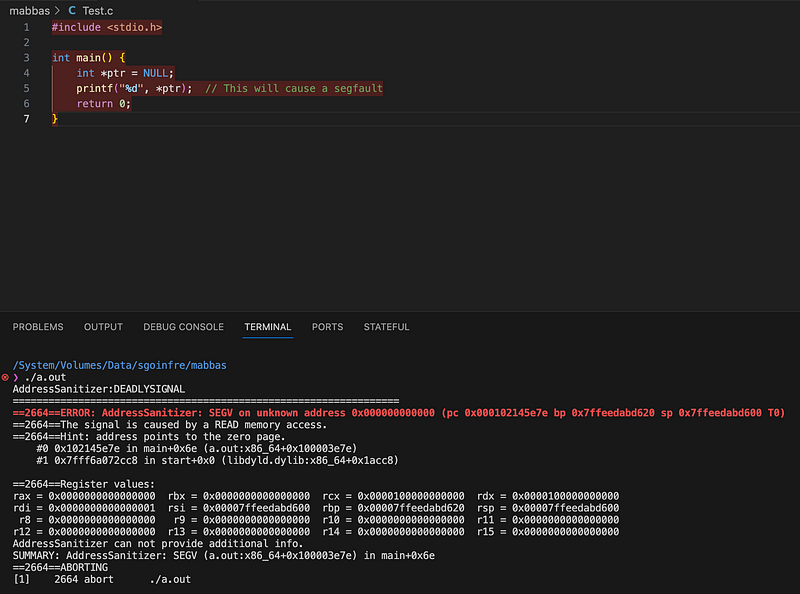
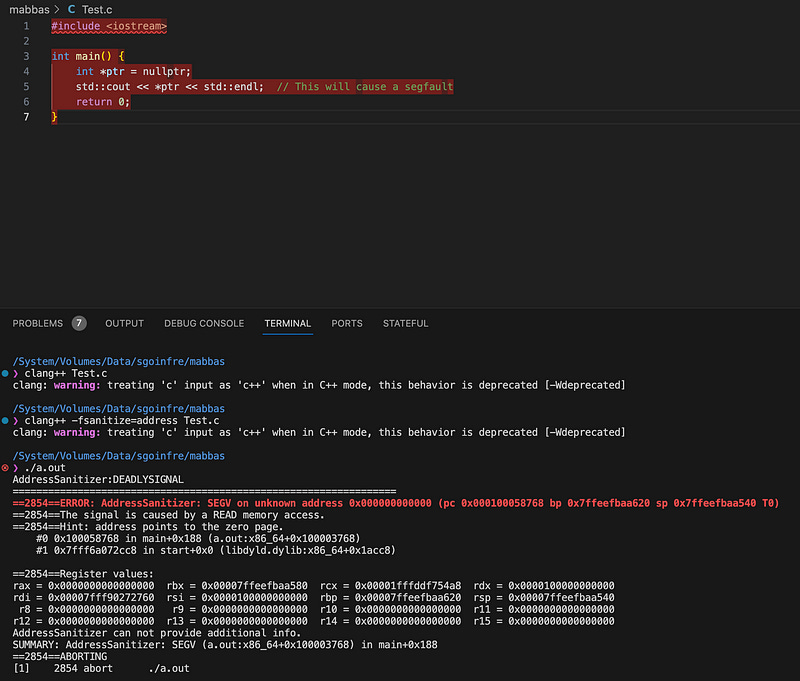
In C, a segfault can occur when you attempt to dereference a NULL pointer or access memory that hasn’t been properly allocated.
Segfault Due to Pointers mismatch:
Causes program termination.
Indicates a severe memory access violation.
A potential sign of a bug in the code, requiring immediate attention.
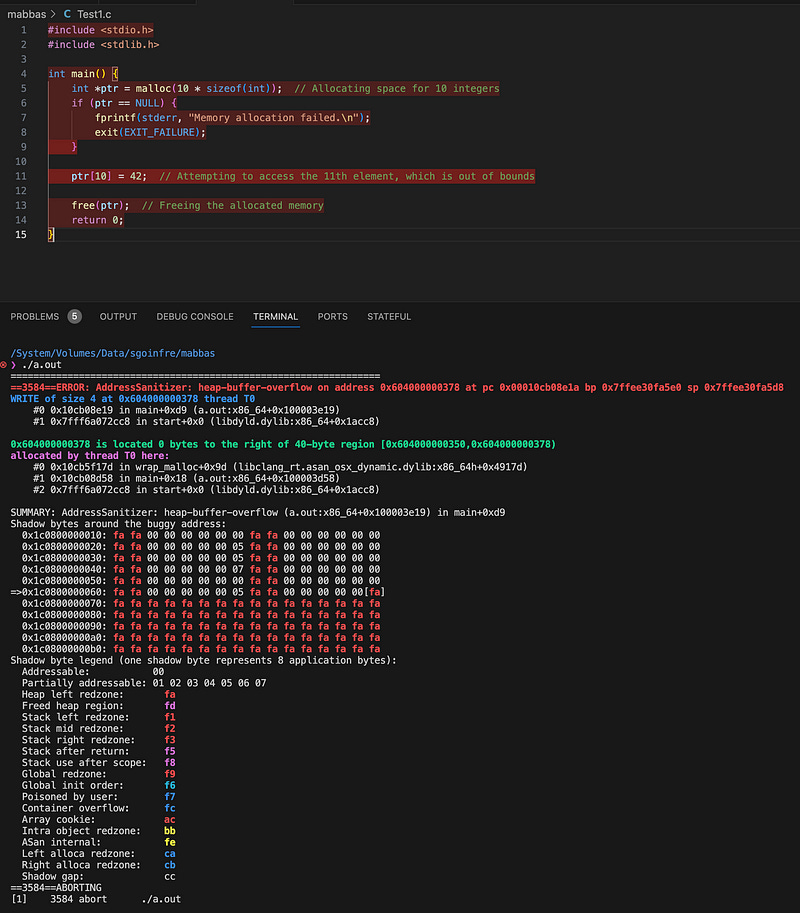
Buffer Overflow:
Buffer overflow is a common security issue where a program writes data outside the bounds of allocated memory. This typically occurs due to inadequate or inadequate bounds checking.
A serious security risk, potentially allowing for code injection and exploitation.
In a brief comparison, while buffer overflows can lead to segmentation faults under certain circumstances, not every buffer overflow will cause a segmentation fault. Similarly, segmentation faults can occur due to a variety of reasons, not limited to buffer overflows.
We gave an overview of Buffer overflow and segfault in above. Now we are going to introduce you to some simple tools to detect this issues in your software. This are my personal preference depending on the environment (Mac / Linux) you are using.
Tools For Detection (Dynamic Analysis)
Mac : Address Sanitizer( use the flag `-fsanitze=address`)
Linux: valgrind / fsanitizer=address
If this somehow helped you understand feel free to buy me a coffee or send me your projects to collaborate. Feel free to reach out in linkedin or slack if you find any mistakes.